As well as Read bucket permissions. For Terraform Enterprise versions before v202203-1 use this command for standalone installations.
Binbashar Tfstate Backend Aws Terraform Registry
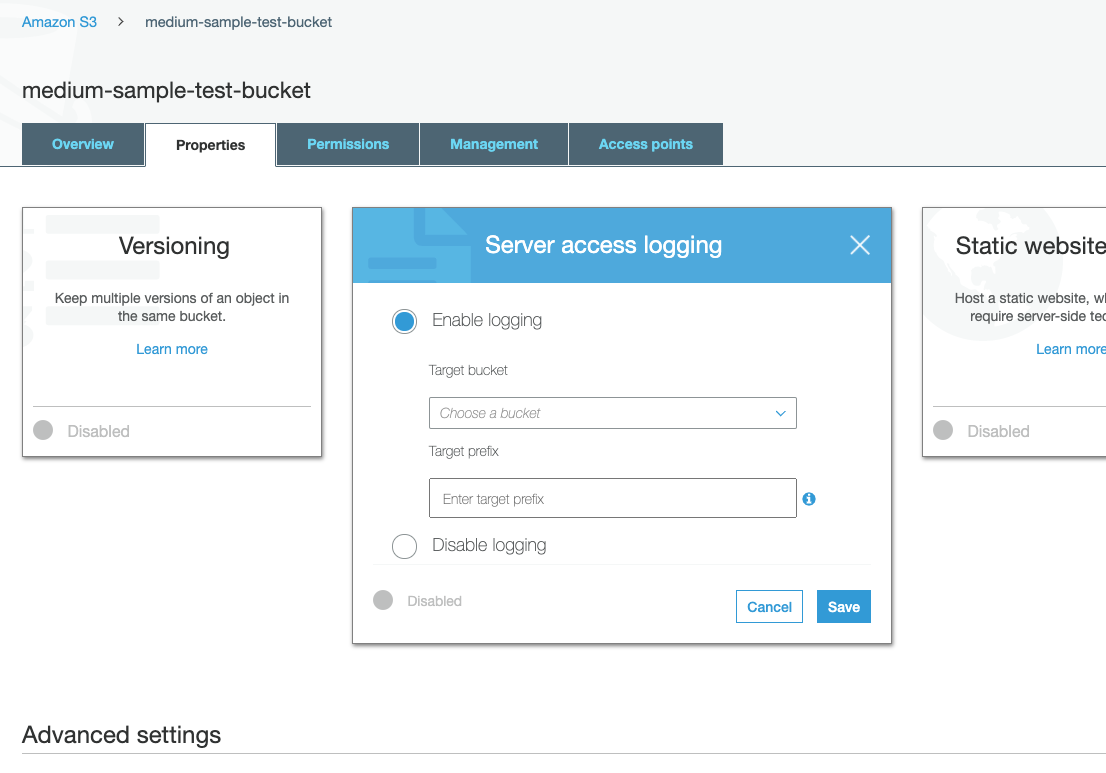
For Target choose the name of the bucket that you want to receive the log record objects.

. StrongDM continues to monitor and manage access to resources even as you use Terraform to provision manage and change your infrastructure. Server Access Logs has been delivered to target S3 bucket. Create a loggingjson file with these contents replacing with your stacks internal bucket name and with the name of your cumulus stack.
This protects the log data stored in your S3 bucket and meets compliance requirements for data at rest. By default Amazon S3 doesnt collect server access logs. When you enable logging Amazon S3 delivers access logs for a source bucket to a target bucket that you choose.
The S3 bucket will be set up so it can only be accessed privately and the EC2 instance will get access to the S3 bucket using IAM. As well as Read bucket permissions. To manage changes of ACL grants to an S3 bucket use the aws_s3_bucket_acl resource instead.
To storage your AWS ELB access log to ASW S3. This bucket is where you want Amazon S3 to save the access logs as objects. StrongDM collects activity logs from human and service accounts across your infrastructure and uses standard message protocols like Syslog to send them to your logging tools.
Edit your S3 bucket to have Server access logging enabled as described here. Provide the name of the target bucket. Navigate to S3.
Elastic Load Balancing supports server-side encryption for access logs for your Application Load Balancer. We use Terraform template below the below. Heres the relevant AWS docs on the matter.
Set the values of your log-delivery-write ACL to allow Logging - Read and Logging Write. This module provides recommended settings. To enable log forwarding set the log_forwarding_enabled Terraform Enterprise application setting to the value 1.
Provision S3 bucket designed for Access Log. For more details see Amazons documentation about S3 access control. Copy and paste into your Terraform configuration insert the variables and run terraform init.
Next we add in the contents for the variablestf file. Each access log file is automatically encrypted before it is stored in your S3 bucket and. These features of S3 bucket configurations are supported.
This module creates an S3 bucket suitable for receiving logs from other AWS services such as S3 CloudFront and CloudTrails. Each access log file is automatically encrypted before it is stored in your S3 bucket and decrypted when you access it. When Amazon S3 receives a requestfor example a bucket or an object operationit first verifies that the requester has the necessary permissions.
Terraform module which creates S3 bucket on AWS with all or almost all features provided by Terraform AWS provider. Navigate to Permissions and select S3 log delivery group and provide access for log delivery. To mount an EFS volume to an EC2 instance using Terraform you can use instance user data to automate this process.
This protects the log data stored in your S3 bucket and meets compliance requirements for data at rest. Enable server access logging for an S3 bucket. The target bucket must be in the same region as the source.
Elastic Load Balancing supports server-side encryption for access logs for your Application Load Balancer. In this story part 2 We going to analyzequery the log information using Athena. If may take a couple of hours to get the access logs in your.
AWS S3 bucket Terraform module. To view the logs navigate to Overview. Ill be using the standard module configuration for this so if you havent already check.
Server access logging successfully enabled. Tfe-admin app-config -k log_forwarding_enabled -v 1. Lets create a separate subfolder 3_ec2_instance in the root folder of our project for the demo Terraform module code.
AWS can control access to S3 buckets with either IAM policies attached to usersgroupsroles like the example above or resource policies attached to bucket objects which look similar but also require a Principal to indicate which entity has those permissions. In the Bucket name list choose the name of the bucket that you want to enable server access logging for. Terraform module which creates S3 Bucket resources for Access Log on AWS.
S3 and IAM with Terraform. Choose Server access logging. Module s3-access-log source tmknoms3-access-logaws version 200 insert the 1 required variable here Readme Inputs 11 Outputs 5 Dependency 1 Resource 1.
In this post we will look at how to set up an S3 bucket and an EC2 instance using terraform. This warning does not apply to new deployments created with version 0280 or later but if. To create a new DynamoDB Test table update the maintf file with the following code.
An access log record contains details about. Type map. For details see Enabling Amazon S3 server access logging.
In part 1 We enabled Server Access Logging to our S3 bucket. Well use Amazon Linux 2 AMI as a base image for our EC2 instance. We create a variable for every varexample variable that we set in our maintf file and create defaults for anything we can.
Connect Terraform Syslog. Description Optional A mapping of tags to assign to the bucket default. Server access log records are delivered on a best effort basis.
Tfe-admin app-config -k log_forwarding_enabled -v 1. Amazon S3 evaluates all the relevant access policies user policies and resource-based policies bucket policy bucket ACL object ACL in deciding whether to authorize the request. For this reason grant cannot be mixed with the external aws_s3_bucket_acl resource for a.
Via AWS Command Line Interface. Both the source and target buckets must be in the same AWS Region and owned by the same account. Terraform Find the S3 bucket used for CloudTrail logging by cross-referencing the aws_cloudtrail s3_bucket_name field with the logging aws_s3_bucket bucket field.
Changes introduced in version 0270 present a HIGH RISK OF DATA LOSS when upgrading from an earlier version. If you use grant on an aws_s3_bucket Terraform will assume management over the full set of ACL grants for the S3 bucket treating additional ACL grants as drift. As you know each AWS region has its own account ID for Elastic Load.
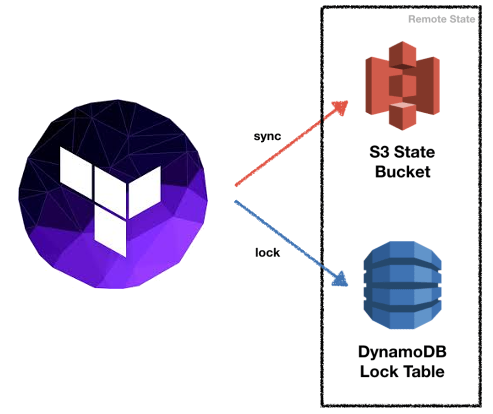
You can go to the S3 Dashboard from the AWS Console to see if the terraformtfstate has been copied or not. The target bucket must be in the same AWS Region as the source bucket and must not have a default retention period configuration. Now again you can create a new resource and see the state will be stored on S3 Bucket.
Using Okta Advanced Server Access Terraform To Automate Identity Infrastructure As Code Okta Developer

Server Access Logging In S3 Cloudaffaire

Terrafom S3 Logging Example Youtube
Binbashar Tfstate Backend Aws Terraform Registry

Server Access Logging In S3 Cloudaffaire
Using Terraform To Create A Vpc Endpoint For Amazon S3 By Bmwitcher Warp 9 Medium
Enabling Server Access Logging Property For All The Objects In Aws S3 By Doyle Wilson Medium

How Do I Prepare An S3 Bucket To Receive S3 Logs Terraform Hashicorp Discuss
Terraform Aws S3 Lb Log Main Tf At Master Tmknom Terraform Aws S3 Lb Log Github
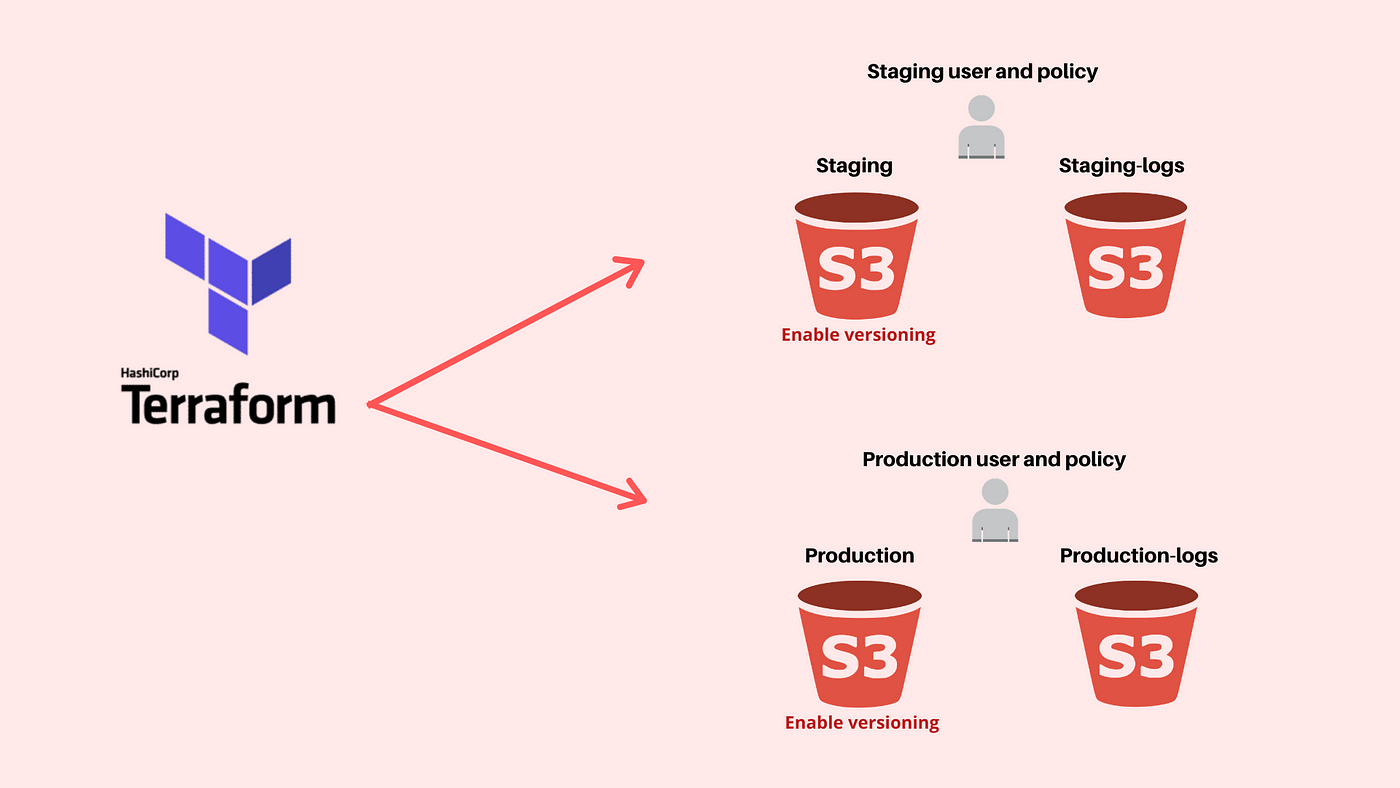
Terraform Create Aws S3 Buckets Staging Production By Jaspinder Singh Medium

Server Access Logging In S3 Cloudaffaire
Terraform Aws S3 Log Storage Readme Md At Master Cloudposse Terraform Aws S3 Log Storage Github

Amazon Web Services Unknown Principle In Bucket Policy Terraform Aws Stack Overflow

Aws S3 Access Logs Amazon S3 Server Access Logging Aws Tutorial Easy Explanation Youtube
Access Logs On Server Side Encrypted Bucket Issue 61 Terraform Aws Modules Terraform Aws Alb Github

Azure Devops And Terraform To Provision Aws S3 My Devops Journal



